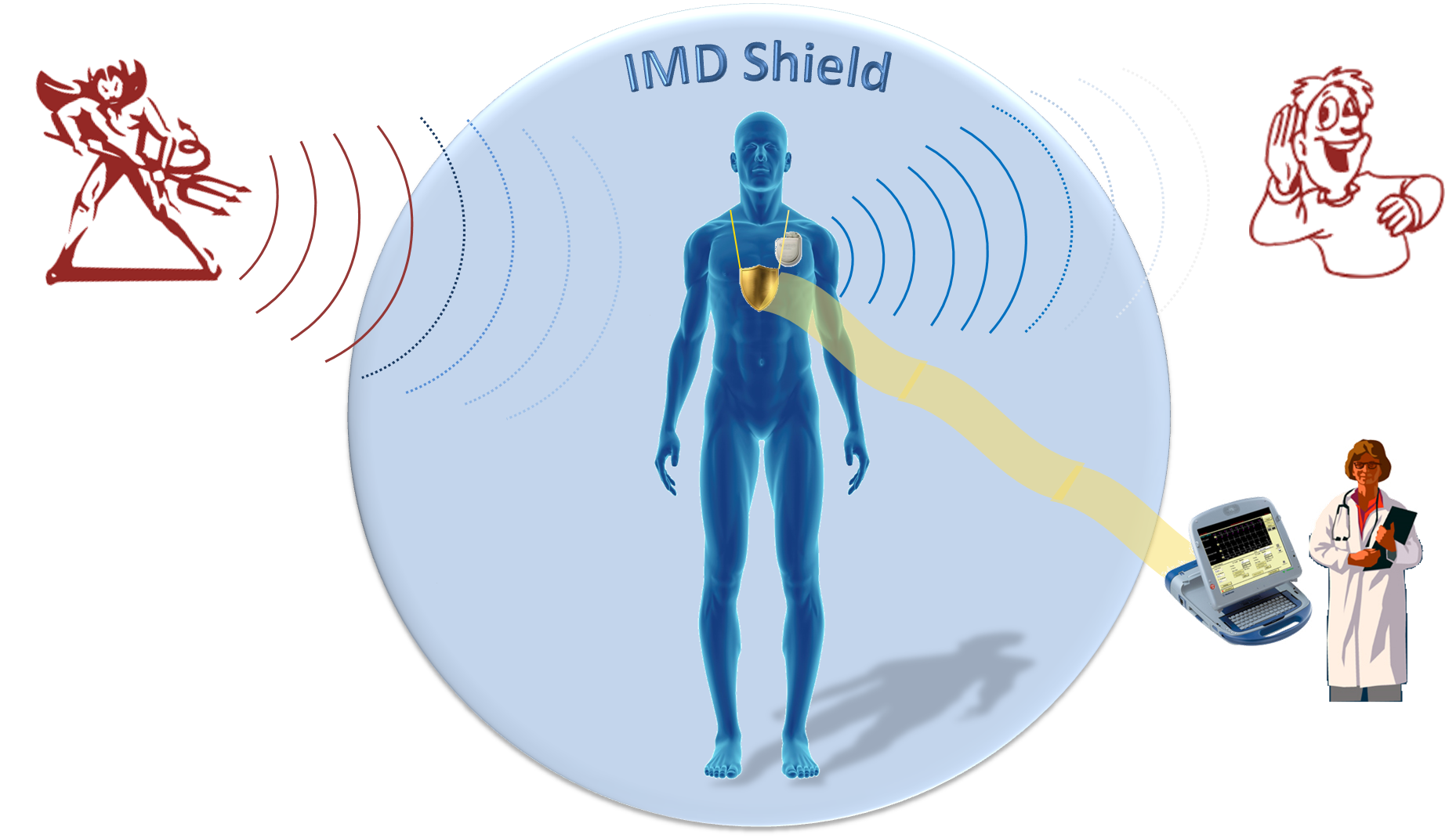
IMD Shield
To achieve our design goal of protecting an IMD without modifying
it, we design a device called the shield that sits near the IMD
and acts as a proxy. An authorized programmer that wants to communicate
with the IMD instead exchanges its messages with the
shield, which relays them to the IMD and sends back the IMD’s responses. We assume the existence of an authenticated,
encrypted channel between the shield and the programmer,
as shown in the figure above.
This channel can be established using either in-band or out-ofband
solutions.
The shield counters two classes of adversarial actions: passive
eavesdropping that threatens the confidentiality of the IMD’s transmissions,
and active transmission of unauthorized radio commands
to the IMD. First, to provide confidentiality for the IMD’s transmissions,
the shield continuously listens for those transmissions
and jams them so that they cannot be decoded by eavesdroppers.
The shield uses a novel radio design to simultaneously receive the
IMD’s signal and transmit a jamming signal. The shield then transmits the IMD’s signal to an authorized endpoint using standard
cryptographic techniques. Second, to protect the IMD against commands
from unauthorized endpoints, the shield listens for unauthorized
transmissions addressing the IMD and jams them. As a result
of jamming, the IMD cannot decode the adversarial transmissions,
and hence the adversary fails to make the IMD execute an unauthorized
command.
Key to the shield’s role is its ability
to act as a jammer-cum-receiver, which enables it to jam the IMD’s
transmissions and prevent others from decoding them, while still
being able to decode them itself. It also enables the shield to detect
scenarios in which an adversary tries to overpower the shield’s
own transmissions to create a capture effect on the IMD and deliver
an unauthorized message. By proxying IMD communications
without requiring patients to interact directly with the shield, our
design aligns with IMD industry trends toward wireless, time- and
location-independent patient monitoring.