Introduction
The past few years have produced innovative health-oriented networking
and wireless communication technologies, ranging from
low-power medical radios that harvest body energy to wireless
sensor networks for in-home monitoring and diagnosis. Today,
such wireless systems have become an intrinsic part of many
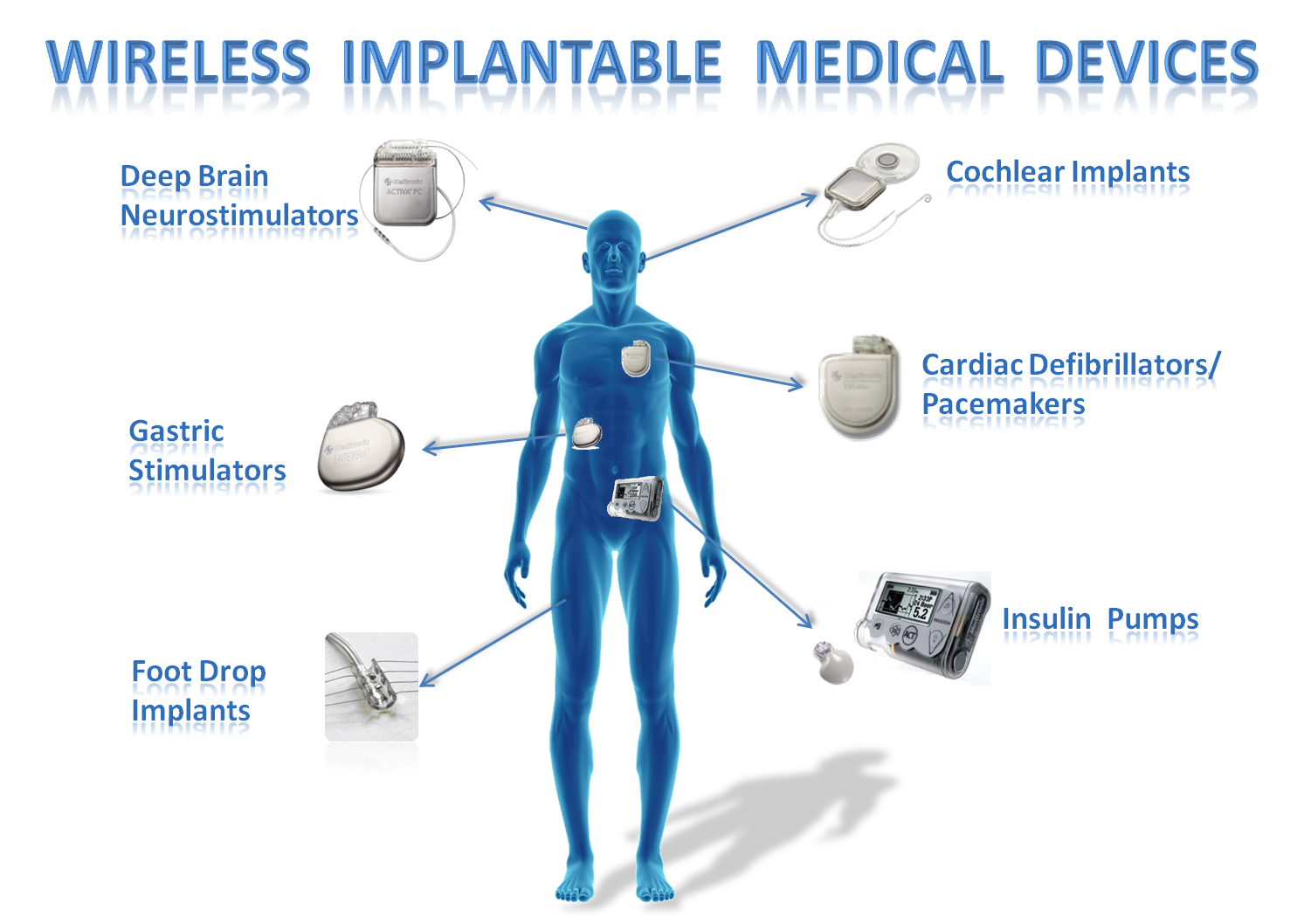
modern medical devices. In particular, implantable medical
devices (IMDs), including pacemakers, cardiac defibrillators, insulin
pumps, and neurostimulators all feature wireless communication
Adding wireless connectivity to IMDs has enabled remote
monitoring of patients’ vital signs and improved care providers’
ability to deliver timely treatment, leading to a better health care
system.
Recent work at the computer science department in UMASS,
has shown that such wireless connectivity
can be exploited to compromise the confidentiality of the IMD’s
transmitted data or to send the IMD unauthorized commands—
even commands that cause the IMD to deliver an electric shock to
the patient. In other systems, designers use cryptographic
methods to provide confidentiality and prevent unauthorized access.
However, adding cryptography directly to IMDs themselves
is difficult for the following reasons:
• Inalterability: In the U.S. alone, there are millions of people who
already have wireless IMDs, and about 300,000 such IMDs are
implanted every year. Once implanted, an IMD can last up to
10 years, and replacing it requires surgery that carries risks
of major complications. Incorporating cryptographic mechanims
into existing IMDs may be infeasible because of limited device
memory and hence can only be achieved by replacing the IMDs.
This is not an option for people who have IMDs or may acquire
them in the near future.
• Safety: It is crucial to ensure that health care professionals always
have immediate access to an implanted device. However, if
cryptographic methods are embedded in the IMD itself, the device
may deny a health care provider access unless she has the
right credentials. Yet, credentials might not be available in scenarios
where the patient is at a different hospital, the patient is
unconscious, or the cryptographic key storage is damaged or unreachable.
Inability to temporarily adjust or disable an
IMD could prove fatal in emergency situations.
• Maintainability: Software bugs are particularly problematic for
IMDs because they can lead to device recalls. In the last eight
years, about 1.5 million software-based medical devices were recalled.
Between 1999 and 2005, the number of recalls of
software-based medical devices more than doubled; more than
11% of all medical-device recalls during this time period were
attributed to software failures. Such recalls are costly and
could require surgery if the model is already implanted. Thus, it
is desirable to limit IMDs’ software to only medically necessary
functions.
This project explores the feasibility of protecting IMDs without
modifying them by implementing security mechanisms entirely on
an external device. Such an approach enhances the security of IMDs
for patients who already have them, empowers medical personnel
to access a protected IMD by removing the external device or powering
it off, and does not in itself increase the risk of IMD recalls.